


Welcome back for another quick dive into security, self-preservation, and fundamentals. With the bear market in full effect, you’d think that the scammers would back off a bit – but you’d be wrong.
This week we’re going to cover a new twist on the same type of mint scam I covered in my “Double-Checking the Checkmarks” article. We’ll also dive into a recent exploit discovered in older versions of the Metamaskextension, and how to manually force an update on metamask.
So, grab your crampons and hide your seed phrase, because we’ve got a climb ahead of us.
If you were around for our last article on mint scams, then you might remember a few of the simple methods we used to see what was going on. This one is a little bit different, but there are still some obvious red flags that we can sniff out.
The setup, though, is the same as the last wave of scams that we saw from verified accounts. This wave isn’t always coming from verified accounts, though, but rather from unverified accounts with a lot of followers. The same basic principle applies; they’re purchasing accounts, still, but just not worrying as much about whether or not they’re verified.
This might be due to so many of the verified accounts already being banned that the “floor price” has increased.
Regardless, the one that caught my notice was a fake Otherside (BAYC) access window, aimed at an already bleeding market.
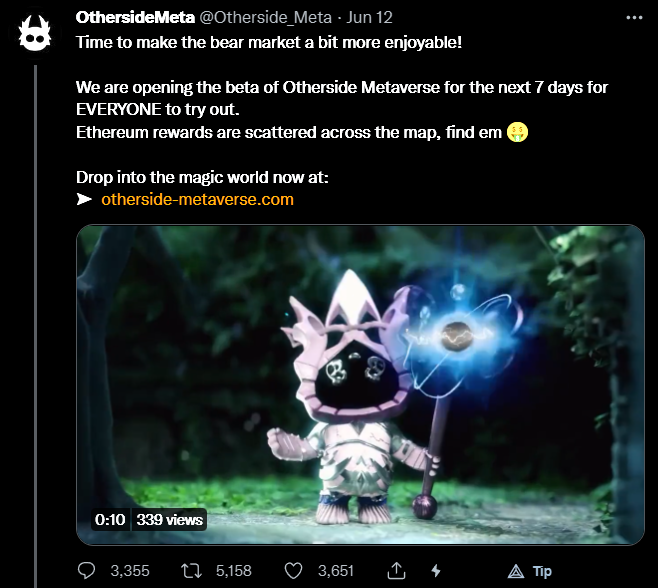
What they’re doing here is priming users to be in a hurry, as the window is “limited” and the rewards are plentiful. There is no window, though, and there are no rewards.
The interesting thing about this scam, is that once you connect your wallet it can view what NFTs you have. If you tried to click through to the Metaverse/mint, though, it scans to see if you have any valuable NFTs or currency. If you don’t, it pops up an error that says you are ineligible.
If you do connect an account with valuable NFTs, though, it pushes through an approval to transfer NFTs. As I did last time, I clicked through to the ‘data’ tab on the approval & immediately noticed some issues.
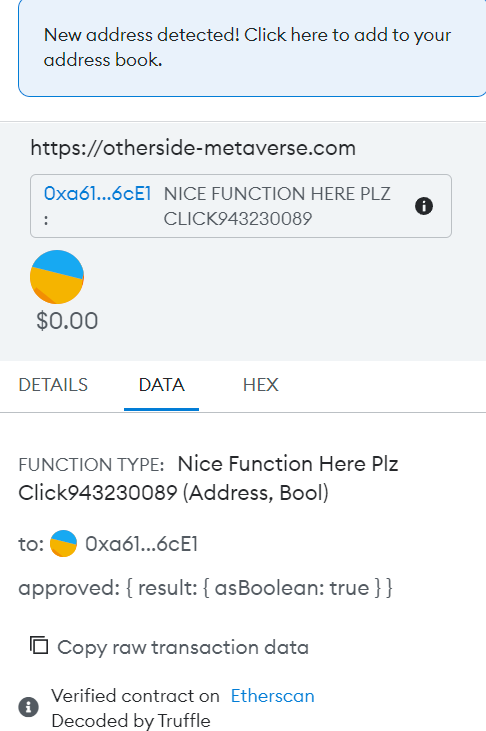
The function clued me in that this was likely yet another scam contract setup purchased on Telegram or elsewhere, and the purchasing scammer didn’t even change the commented values to make it less obvious.
Again, it doesn’t take a genius to steal.
Viewing the associated contract on Etherscan, it actually flagged as connected to the ENS Token Tracker. Why that happened is above my pay grade, honestly, and if any of my readers are more familiar with why this would’ve happened, feel free to hit me up on Twitter.
What I can tell you is that viewing the contract on Etherscan showed that it included a function for transferring NFTs, and a quick glance at incoming & outgoing transactions showed more than a few already pilfered from the unwary.
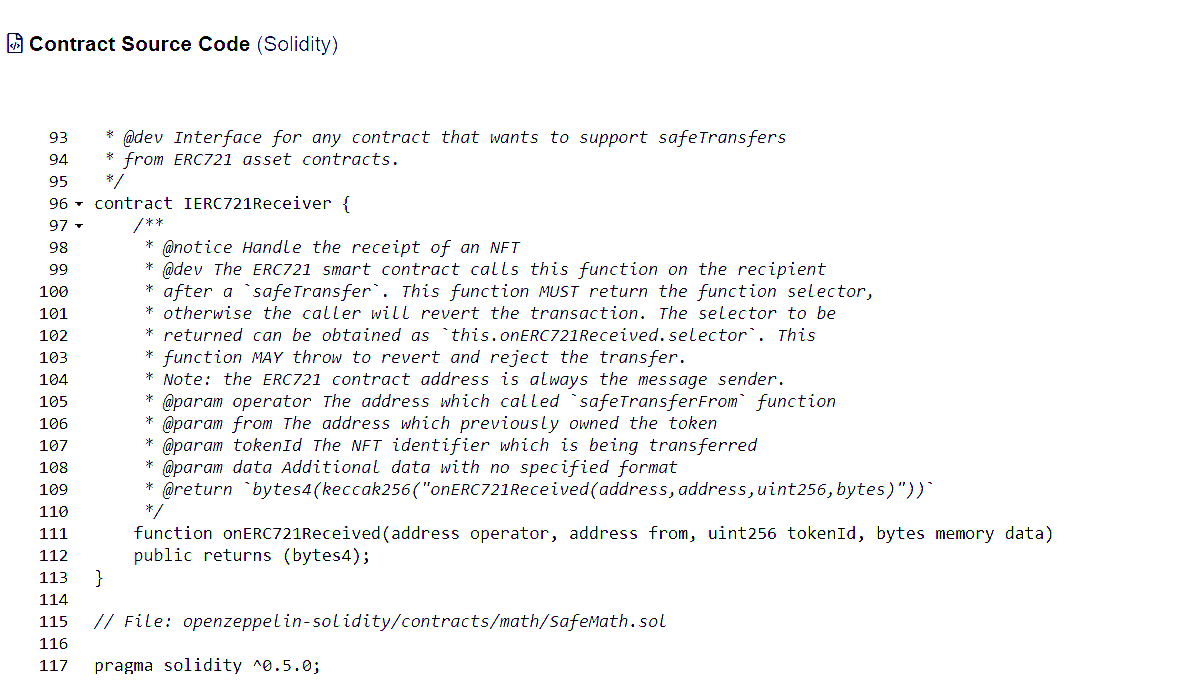
I was able to reject the approval request & disconnect from the website with no issues. As ever, the best habit you can get in is taking a few extra minutes to verifying website addresses & approval data & contracts, before approving anything.
It is very easy to get in the habit of just approving view access or other simple requests, but that is very often how we get burned. Take a deep breath and a few extra minutes. No “window” is worth risking your account over, and you can usually catch a lower price on secondary, anyway.
On June 15, 2022, the Metamask team disclosed a huge vulnerability in some previous versions of their Metamask browser extension.
Only a small segment of users might have been affected, specifically if all three of the following conditions are true:
This should also only be a problem for users of extension versions 10.13.3 and earlier, though, and most often your metamask will be fully updated.
How do we check, though?
What you’ll want to do is right-click the Metamask icon in your browser and select Manage extension.
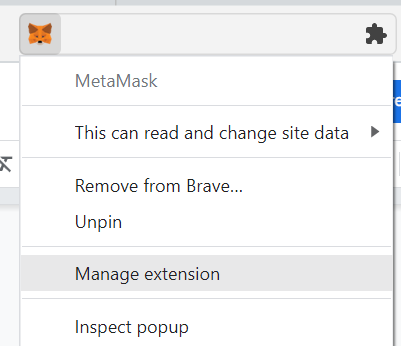
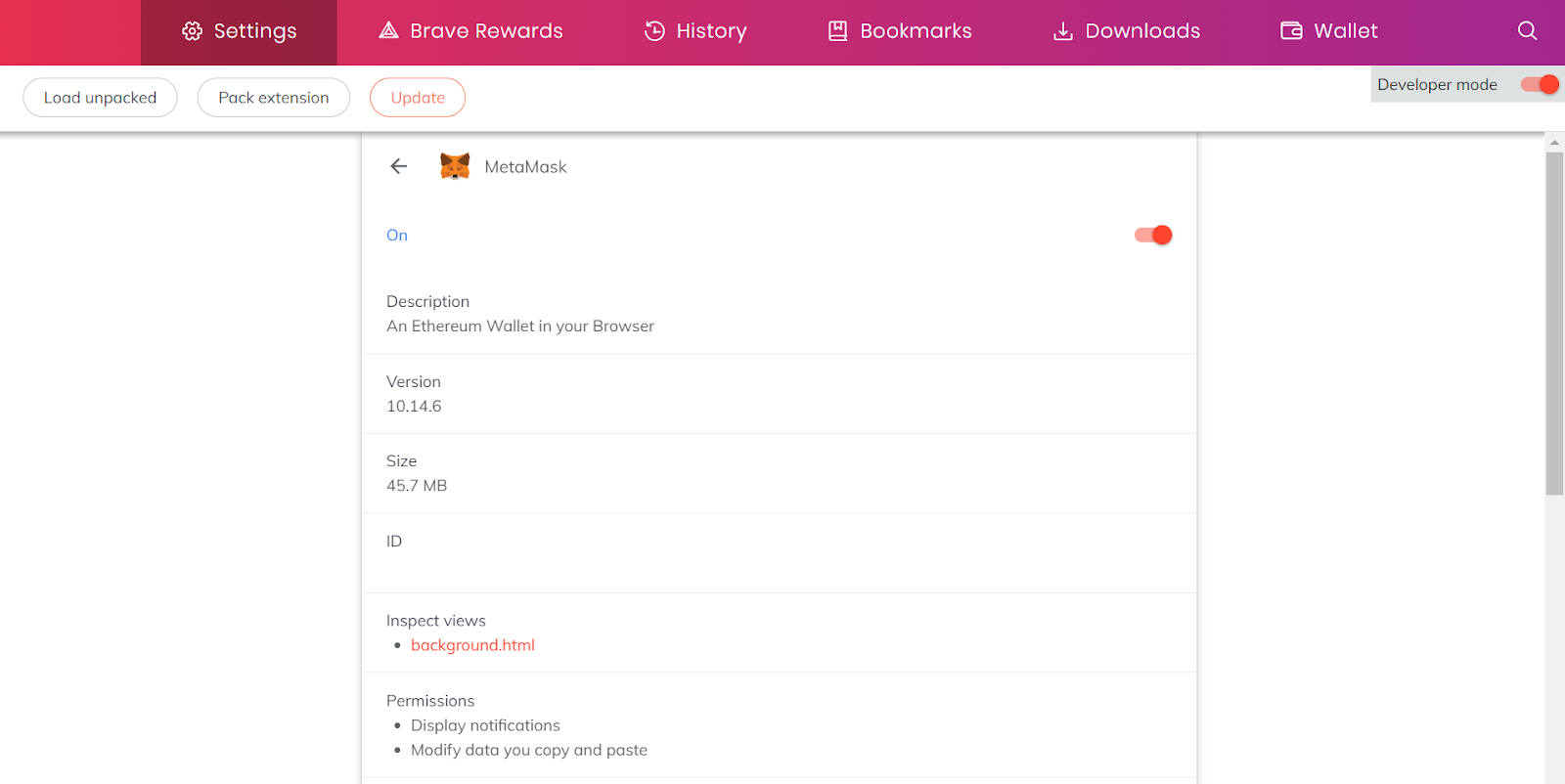
This will bring up a page showing some basic information about the extension, along with what version you have installed. From here, you’ll want to click the ‘Developer Tools’ toggle in the top-right corner, and turn it on.
This will add a few more options to the page, including one for manually forcing an update, as shown in the image below. I’m using the Brave browser, but most of them should be roughly the same.
You can go ahead and click ‘Update’ from here, if you’d like, and just be sure to check back regularly to make sure your extension is up to date. It actually functions in much the same way for most extension-based web3 wallet solutions (Phantom, etc), so keep that in mind in case any more vulnerabilities or exploits are found.
Also, be sure to give thanks to the fine folks at Halborn Security, who disclosed this bug through official channels, in return for a $50,000 bounty that honestly may not be close to enough. It is whitehats & cybersecurity professionals like them that help keep us all safe from even more loss-producing events in crypto, and I personally can’t thank them enough.
Until next time, keep an eye on your OpSec and your mind on the fundamentals.

Torrent/seedbox aficionado, decentralist, cultural archivist, fundamental analyst, podcast addict, shitcoin-sifter extraordinaire
Tip Jar
BTC: bc1qahxrp47hpguhx8y8r382dekgca34tlv54aufht
Doge: DJRy9gGSUGeyXfVcZXzKLkBv7RmDLv3MhJ
Share This Article
Join 10,000+ forward thinkers! Get crypto education in your inbox.