WTF is OPSEC and why you should be aware of your own activity and the trail you leave on a permanent public record for all to see!
Over the last few weeks we’ve been discussing privacy, zkrollups, and just how important they can be as we move forward. In my last article, I mentioned the need for a discussion of OpSec and safety, and how hard that can be to navigate amidst public ledgers & tokenized assets tied to your social media accounts. This week, we’re going to dive into the why and a few ways that you can cover your assets.
Clout-based Risks
I’m calling this section “clout-based” risks, because honestly that’s all you stand to gain by exposing yourself in this way. I’m specifically referring to anything you post publicly that ties specific assets to your account. This can be using an NFT as a profile picture, using an ENS domain in your display name, or taking straight screenshots of purchases.
Honestly, there’s a lot of ways you might be oversharing & compromising your account, including posting your address in giveaway threads, etc. – but these are the ones folks don’t always consider, because it takes a little bit more leg work to trace them to an account.
With an ENS domain tied to your display name, it’s as easy as a quick search to connect that name to the public address of your account – that’s essentially the point, but just as having the ENS displayed makes it easier for folks to know where to send things for you – it’s just as easy to track every move that you make.
Similarly, tracing a pfp (profile picture) is just as easy. If you have a Bored Ape pfp, I know to look at that collection. Then I narrow down the traits that I can see until I find the exact NFT; even easier if they list the id # of the NFT, since you can just search for that.
At this point, that address is exposed. Your buys & sells are traceable, and if you’re holding too much value in that wallet: congratulations, you’re now a prime target for hackers & phishermen.

Mitigation
Now that we’re aware of the problem – how do we solve it? Well, the easiest suggestion is to not worry about clout – but that’s a hard sell when you’re personally invested & want to help promote the project by putting the art out there for other people to see.
The next best solution is to treat your public-facing addresses with caution & suspicion. Set them up with the intent of them being visible, and utilize mixers or migration from a privacy-focused L2 to fund the wallet.
That is, use a newly-created fresh address to purchase your ens domain & displayed NFTs, and only fund it through mixing or other privacy-preserving mechanisms. In this way, you lower the odds of someone tracing anything you purchased back to your main accounts.
Partitioning is one of my favorite safety precautions, and that’s what we’re utilizing here. You mentally note that the exposed address is “public”, and you never directly touch it using your other, unexposed accounts.
Learning to partition funds is a great way to mitigate risk, in general, since you’re limiting the risk to your overall holdings by separating them. I’ve seen folks buy hardware wallets & use all sorts of fancy solutions to keep their assets safe, but if you make a big enough mistake it doesn’t matter how good your cold storage solution is.
Segregate funds. If you look at your balance and ever think, “wow, that’s a lot of money” – you need to divide it amongst multiple accounts & wallet solutions. Be keenly aware of wallets & addresses you access via mobile or shared computers, because those will be facing the most risk.
An Eye on Approvals
This is more about safety than OpSec, but historically one of the biggest “exploits” for stealing assets has been metamask approvals. You see these so often, usually requesting “view” access to your accounts & addresses, and it sort-of becomes second-nature to approve & move on.
It doesn’t help that so many pages ask for access the second you’re on-site. This is necessary, but the tedium of it can drive you to complacency where approvals are concerned.
Consider the Polygon NFT airdrop exploit, a while back. Now, some folks who lost BAYC & other blue chip NFTs will tell you that just receiving or clicking one of these airdropped NFTs allowed the hacker to steal everything they had.
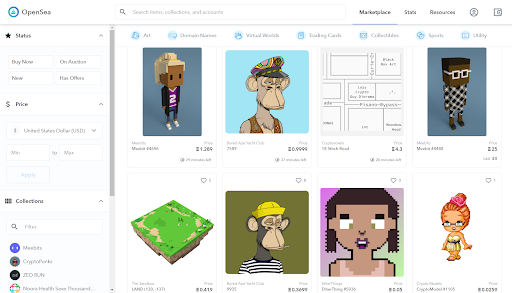
That is patently false, because if it were that easy then none of us would have any crypto. What is actually happening is the cheap-to-transfer Polygon NFTs injected javascript into OpenSea, and when you clicked on them they would pop up requests for two approvals. You actually have to approve these before anything is transferred; there is no way they can steal anything without you doing this.
From the screens I’ve seen, it looks like these are obviously transfer approvals, which should have given folks pause (because they weren’t TRYING to transfer anything!), but I’ve also seen contracts that are just requesting more access in the approval, rather than an outright transfer.
CryptoCat on Twitter wrote a solid thread on “approval hygiene”, and looking more closely at contracts before granting access – but I’d say at the very least you should read any transfer or approval request that comes through, closely, before approving. Is it only asking to view your addresses & assets, or is it requesting more access or to transfer funds? How much are they trying to transfer? Is it the mint price, or is it drastically more?
Opsec Tools & Tips
The most important thing you can do to protect yourself is to take an extra ten seconds to confirm things before approving any transaction. This better protects you from exploits, but it also helps protect you from yourself & simple mistakes. There is not a hardware or software solution in existence that can keep you safe if you’re careless.
That said, one great tool CryptoCat mentioned in the above-linked thread is revoke.cash; it allows you to plug in your addresses & see what approvals you’ve granted to OpenSea and others. It is a good idea to check this every so often, and revoke approvals to sites/contracts you no longer use – assuming it’s more cost-effective than just creating a new address & migrating.
There will be a fee associated with either, so make sure to check ETH Gas Station or similar sites & time your approval checkup accordingly.
Lastly, be aware of what you are downloading. I do a lot of research & vetting of projects, and you always have these super early builds of wallets, games, apps, etc. that you have to try out as part of the review process. You always want to make sure you’re running a scan (not just your antivirus) before you open them, regardless of source or file type.
One thing to remember is that a lot of crypto software & miners are flagged by your AV/Malware software, anyway, so that doesn’t serve to protect you from much since you’ll be whitelisting most things, regardless. Best practice is opening things in a virtual environment like “Sandbox” in Windows 10 Pro, or otherwise as explained here.
VirusTotal is another great tool that allows you to link or drop a file & quickly see interactions & issues, and potentially a history of file versions as submitted by the community.
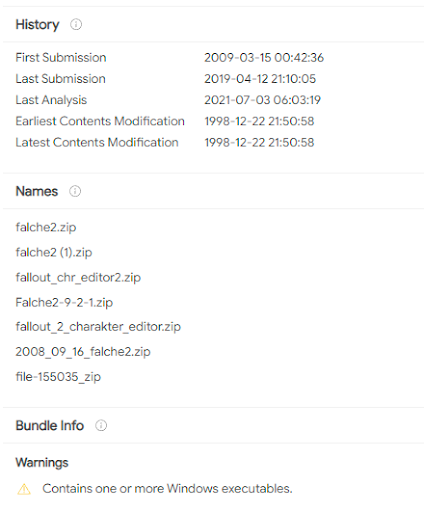
In the above image, I’ve just dropped a zip containing a character editor for an old game. I know it’s safe, but this shows you some of the information you’ll get from virustotal. I’ve also used this in the past to help determine what sites & third parties are contacted by software. Below is an old scan I’d done of the BitTorrent Token software, demonstrating potential risks for torrent users utilizing it.
Again, very handy.

Last but not least, documents. We haven’t always worried so much about documents, but malicious pdfs & even Google Docs are spreading like wildfire with the crypto boom. Treat every Google Drive or Doc link as malicious, and only open them if you are getting the link from a friend you trust – and even then consider opening them in a sandbox or remote environment, and not connected to your main Google account.
With PDFs and other documents, you can use this free tool from Ty Labs to scan whitepapers, litepapers, and other pdfs that you might be reviewing.
Hopefully this article has been helpful in making your accounts a little safer, and being aware of your fundamental health & approval hygiene. Until next time, remember to cover your assets.
Related: Metamask Wallet Safety
Author
-

Torrent/seedbox aficionado, decentralist, cultural archivist, fundamental analyst, podcast addict, shitcoin-sifter extraordinaire
View all posts
Tip Jar
BTC: bc1qahxrp47hpguhx8y8r382dekgca34tlv54aufht
Doge: DJRy9gGSUGeyXfVcZXzKLkBv7RmDLv3MhJ